GLOSSARY
Definitive Guide to Ransomware: Understanding, Preventing, and Responding to a Ransomware Attack
A guide to defining, explaining, and understanding ransomware to bolster your organization’s security posture against attacks.

Understanding ransomware
Ransomware threats are a relevant part of any organization’s risk landscape awareness. And as threat actors and their TTPs become more advanced, ransomware groups are becoming more aggressive and taking on a growingly diverse range of targets. Understanding what ransomware is, what risk it presents for your organization, and how to build an effective response and recovery plan are all crucial for implementing a strong threat intelligence program and keeping your assets, infrastructure, and personnel secure.
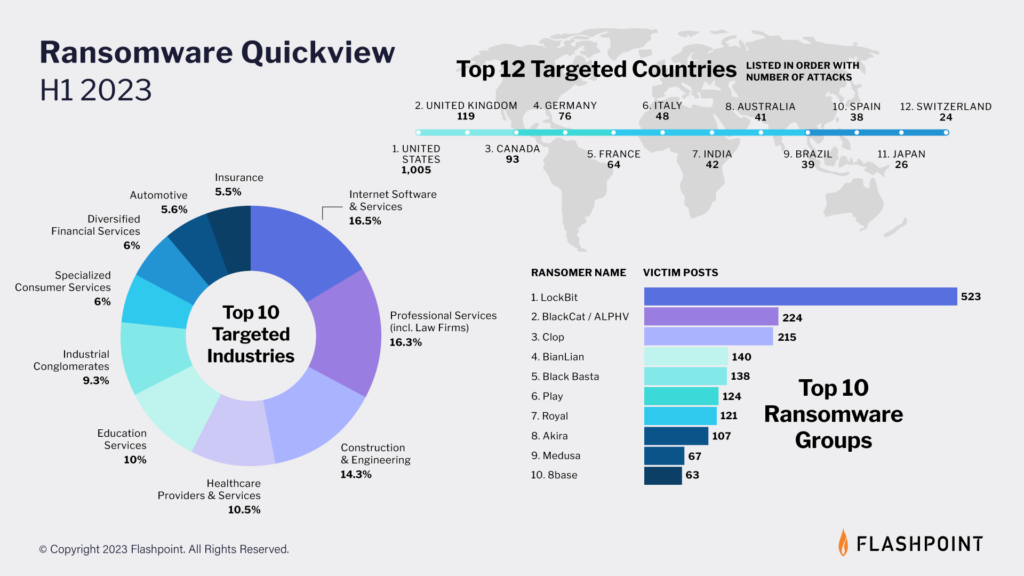
In this article, we:
- Define ransomware and overview its history, including notable attacks
- Outline types of ransomware and how attacks occur
- Explain what measures your organization can take to remediate ransomware risk and respond and recover to an attack
What is ransomware?
Ransomware is a specific type of malware that locks up the victim’s files, making them inaccessible. It uses data encryption to block organizations’ access to their own sensitive data, demanding a ransom is paid to unlock it safely. Personnel facing a ransomware attack are denied access to internal files and programs, and ransomware actors often design their malware to spread throughout an organization’s infrastructure while targeting its entire database and file servers, more effectively forcing the company to pay the ransom.
As attacks evolve to become more severe, threat actors have also adopted tactics to add external pressures, such as threatening to release confidential information, doxx executives, or inform clients that the company is not willing to pay to protect their data, to increase the likelihood of payment.
The history of ransomware
The journey of ransomware from its inception to its current state reflects a mix of evolving tactics and increasing aggressiveness. Originating with the earliest recorded ransomware attack, a malware disguised as the AIDS Trojan and delivered via floppy disk in 1989, ransomware initially existed as simple attacks with limited reach.
Until the 2000s it was difficult to efficiently receive ransom payments, making ransomware attacks relatively rare compared to today. Threat actors usually collected payments through money transfer services like Western Union or MoneyGram, or would request users to send prepaid debit cards through services like MoneyPak. With the advent of cryptocurrency, it has become much easier for threat actors to receive payments and quickly profit, which has led to this type of attack becoming more widespread.
As technology advanced, so did the ransomware, with notable strains like LockBit, Conti, and Clop causing global disruptions. In recent years, ransomware has grown from a digital nuisance to a significant security threat, with attackers even offering Ransomware-as-a-Service (RaaS) platforms to less technically inclined criminals.
How ransomware works
The typical ransomware attack follows a set pattern:
- Infection: The ransomware is introduced to the victim’s system through various means, such as phishing emails, malicious downloads, or exploiting vulnerabilities.
- Encryption: Once activated, the ransomware scans and encrypts the victim’s data.
- Ransom Note: The victim is then presented with a note demanding a ransom payment, often in cryptocurrency, in exchange for the decryption key.
Recommended Reading: The Seven Phases of a Ransomware Attack: A Step-by-Step Breakdown of the Attack Lifecycle
Ransomware often finds its way into systems through various means. Phishing emails remain a top method, tricking users into downloading malicious attachments. Drive-by downloading—where users inadvertently download malicious software by visiting an infected website—and the exploitation of software vulnerabilities are other common tactics that allow ransomware strains to move laterally within networks and infect systems.
Forms of ransomware
- Encryptors: Encrypts data, rendering it inaccessible.
- Doxware/Leakware: Threatens to leak confidential information.
- Scareware: Mimics system issues, prompting users to pay for a fake solution.
- Lockers: Locks out users from their devices.
- Ransomware-as-a-Service: Outsourced ransomware attacks for a share of the profits.
The impact of ransomware
Ransomware attacks can be devastating. Beyond the immediate financial cost of paying the ransom, victims may face operational downtime, reputational damage, and legal repercussions. For many, the dilemma isn’t just about paying the ransom but also grappling with the consequences of potential data loss or the ethical implications of funding criminal activity.
Notable ransomware groups and attacks
LockBit
LockBit is a ransomware-as-a-service group that has been active since 2019. The group has gained notoriety for its sophisticated and ruthless strain of ransomware. It infiltrates computer systems, encrypts vital data, and demands hefty ransoms, leaving victims grappling with difficult decisions.
LockBit has been the dominant strain of ransomware over approximately the past year. According to Flashpoint data, it has accounted for 21.99 percent of all known ransomware attacks from October 2022 to September 2023.
Clop
Clop (also known as Cl0p) is an extortionist ransomware-type malware that originated in 2019 and operates on the Ransomware-as-a-Service (RaaS) model. In 2023, Clop made headlines leveraging two vulnerability exploits against their victims: GoAnywhere MFT and MOVEit. Both data compromise events resulted in hundreds of victims being listed on the clop ransomware leak site.
Lessons From Clop: Combating Ransomware and Cyber Extortion Events
Recent attacks from Clop emphasize the importance of implementing an organization-wide ransomware and cyber extortion strategy, from preparedness to detection and isolation
WannaCry
The WannaCry ransomware attack of May 2017 affected Microsoft Windows users worldwide, encrypting data and demanding Bitcoin ransom payments. This mass attack targeted organizations around the globe, using EternalBlue, a Microsoft exploit developed by the NSA for older Windows systems. This exploit was stolen by hacker group The Shadow Brokers and subsequently leaked roughly a month before the attack, which allowed for the ransomware’s rapid propagation to a large number of countries across industries.
Related Reading: Linguistic Analysis of WannaCry Ransomware Messages Suggests Chinese-Speaking Authors
Petya
Petya is a strain of ransomware that targets Microsoft systems, encrypting data and preventing the operating system from starting. First observed in March 2016, it demands ransom payments in Bitcoin and was initially propagated via email attachments, although there have since been attacks using Petya malware that use a variety of TTPs to do damage.
One of its most notable variants, dubbed NotPetya, emerged in June 2017 and was used to carry out a widespread ransomware attack around Europe and the US. These attacks primarily targeted Russia and Ukraine, and are believed to be politically-motivated attacks against Ukraine that took place on its Constitution Day.
Conti
Conti ransomware, which has existed since 2020, utilizes a number of TTPs to distribute the malware, including spear phishing campaigns, weak RDP credentials, and the exploitation of vulnerabilities in external assets. In February 2022, Conti chats were leaked, identifying individuals involved with the ransomware group and exposing other details of how it is run. However, there is evidence that Conti is still operating despite the leaks, and is still an active threat in the ransomware space.
Related Reading: Conti Affiliate Leaks Ransomware Documents
Colonial Pipeline
Carried out by criminal hacking group DarkSide, a ransomware attack was leveraged against American oil pipeline system Colonial Pipeline in May 2021 that led to the suspension of all pipeline operations in an effort to contain the attack. Working with the FBI, the organization made a payment of 75 bitcoin, approximately $4.4 million, to DarkSide, making it the largest attack on an oil infrastructure target in American history. They were subsequently provided an IT tool by the threat actor group to restore the system. It was announced in June 2021 that 63.7 of the bitcoin, or $2.3 million of the total payment, had been recovered.
Related Reading: DarkSide Ransomware Links to REvil Group Difficult to Dismiss
Kronos
In December 2020 a ransomware attack against workforce management company Ultimate Kronos Group left many organizations, including some major enterprise companies, unable to process payrolls and consequently in violation of their obligations to employees. UKG was subsequently sued by several of its customers for alleged negligence in security practices and data protection, highlighting the importance of organizations implementing best practices to protect their and their users’ data.
Recommended: The Great Cyber Exit: Why the Number of Illicit Marketplaces Is Dwindling
Ransomware susceptibility
As your organization takes steps to strengthen its defense against ransomware attacks, it’s helpful to identify things that make your personnel and infrastructure more susceptible to being targeted by threat actors. This knowledge can assist you in understanding what steps to take to better protect your organization from a successful ransomware attack.
What do threat actors look for to target organizations?
Some of the key weaknesses that are in your control that threat actors look for to make for an easier attack include:
- The use of outdated devices or software, which increase the likelihood of there being exploitable vulnerabilities in your systems that threat actors can gain access through
- Browsers or operating systems that are not patched
- A lack of a proper backup, making the use of malware to encrypt an organization’s file and data more harmful and easier to leverage a ransom payment from
- Cybersecurity awareness and training that has not been prioritized, increasing the chances that an attack will be successful and the organization will not have a coherent defense response
Additionally, there are other elements that may make certain companies more susceptible to ransomware attacks that are not necessarily changeable, but are important to be aware of to emphasize the importance of a strong ransomware prevention and defense plan.
Many companies targeted by ransomware attacks:
- Possess valuable, accessible data that a ransomware actor can steal. This both raises the chances that an organization will pay to retrieve it, and gives the threat actor a backup since it’s more likely that third parties in underground communities would be willing to pay for the stolen data if the organization refuses.
- Are large enough to have the resources to pay a higher ransom fee. Many ransomware actors are motivated by money, which means targets that are in a position to pay more per attack are favorable. The entertainment industry is one of the most-targeted categories because its companies often have the funds and motivation to pay more to regain their stolen files.
- Have more potential for damage. Although financial motivations are often a primary concern in the ransomware space, some threat actors execute these attacks for the purpose of causing widespread harm that amplifies its impact. Supply chain companies are one example of an organization type that has the ability to cause damage to multiple other companies during a single attack, which makes them a bigger target for threat actors.
- Have many remote workers. Working remotely requires heavier use of softwares and systems that may have vulnerabilities threat actors can take advantage of. Organizations that employ more remote workers may be viewed as better targets by ransomware actors looking to exploit infrastructure weaknesses to spread their malware.
Preventing a ransomware attack
With all of these factors in mind, it’s important to have a realistic view on how ransomware risk fits into your organization’s broader threat landscape analysis. Having a strong threat intelligence program in place is a good start to protecting your assets and infrastructure from an attack, but it is only one part of building a good defensive strategy.
A robust cyber awareness training program is one of the most impactful ways you can preempt potential threats. An effective program educates all of your employees about best cybersecurity practices and teaches them how they can contribute to a more secure organization, minimizing the risk of successful ransomware distribution through methods like email phishing. Best practices for individuals include:
- Not clicking on suspicious email attachments or interacting with links that could contain malware
- Not sharing personal information that could assist threat actors in accessing your personal system or device to infiltrate your organization
- Keeping operating systems and applications up to date to take advantage of the latest security patches that help protect your files and device
- Avoiding the use of unknown USB sticks or unverified download sources that could contain malware to infect your device
- Using a VPN when connecting to public WiFi networks
In addition to these steps each employee should take to help prevent a successful breach, there are broader organizational measures that can be enacted to further impede threat actors from executing a successful ransomware attack. These include:
- Having a strong data backup: Since a ransomware attack relies on blocking organizations’ access to their files and data, having a robust backup means that if your original assets are encrypted, you still have access to your infrastructure. It’s important to protect this backup so that it cannot also be encrypted and leveraged against you during an attack.
- Strengthening user authentication and other policies: Exploiting RDP vulnerabilities is one of the most common ways threat actors gain access to devices and data to encrypt. As an organization, requiring employees to have strong passwords and use MFA can prevent the success of these TTPs. It’s also best practice to limit each individual’s data access to only what they actually need to complete their jobs, which minimizes the access a threat actor can get to an organization’s files from any one employee.
- Investing in a robust anti-ransomware program: Using virus scanners and other ways to filter content sent to your employees prevents distribution attempts that are propagated through personnel. It’s also important to consider that some threat actors use other TTPs or well-researched and advanced spear phishing attacks that can be successful against even the most conscientious employees, so it’s crucial to have a backup plan to defend against an attack if malware does infect your organization’s systems. Implementing programs that can detect possible malware behavior and stop the encryption of files before you can no longer access them gives you a safety net if ransomware is distributed to any of your organization’s devices.
- Implementing tabletop exercises and cyber extortion-specific training: Having discussions before an attack to prepare your teams for their role in a potential attack strengthens your response plan and supports involved parties in better executing their parts if an attack does occur. Similarly, company-wide training that educates employees on common threat actor TTPs, like social engineering, helps preemptively combat attacks by lowering the chance that an individual will fall victim to a ransomware actor’s attempts to infiltrate your organization.
- Maintaining an IR playbook: Keeping an updated playbook that contains resources and capabilities of your organization works two-fold to help optimize your response to a ransomware attack. By ensuring you are staying current with your response plan by keeping the playbook updated, and by consistently working to improve your plan and expand its resources, you are better positioning your company and teams to act quickly during an emergency.
Ransomware defense and mitigation
Ransomware attacks typically follow a certain sequence, starting from initial entry and ending with data encryption. Understanding this chain can offer crucial interception points:
- Initial Entry: Often achieved through phishing emails, malicious downloads, or exploiting software vulnerabilities.
- Establishment: After entry, the ransomware tries to establish itself, often using techniques to evade detection.
- Propagation: Ransomware can spread to other connected systems, seeking to maximize its impact.
- Encryption: The end goal: locking users out of their data.
Layered defense strategy
Given ransomware’s versatility, a single defense layer is insufficient. A multi-layered strategy is essential:
- Endpoint Protection: Advanced endpoint protection platforms (EPP) can preemptively identify and thwart threats.
- Network Monitoring: Detect abnormal patterns in network activity using Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS).
- Email Filtering: With phishing being a top vector, strong email filtering tools can prevent many attacks at the outset.
- Regular Patching: Keeping software updated can prevent attacks that exploit known vulnerabilities.
Data backups
Effective data backups can render a ransomware attack impotent. Remember:
- Isolation: Ensure backups aren’t connected to your primary network.
- Testing: Regularly test backup integrity to ensure a smooth recovery process when required.
Incident Response Plan
Every organization should have an incident response plan that clearly outlines:
- Initial Action: Steps to confirm and report a ransomware attack.
- Containment: Strategies to halt the spread of the ransomware.
- Recovery: Detailed procedures for system restoration from backups or other methods.
- Communication: How and when to communicate about the attack, internally and externally.
Ransomware Attack Response and Recovery
A proactive approach is paramount, but when ransomware does strike, a swift, coordinated response can be the difference between a minor disruption and a major catastrophe.
Engaging with state-of-the-art threat intelligence platforms can offer proactive defense benefits. By understanding ransomware’s tactics, techniques, and procedures (TTPs), you can preempt potential attacks and gain critical context to respond to an attack quickly.
1. Evaluate and Isolate
- Swift Validation: As soon as an attack is suspected, verify its authenticity.
- Scope of Attack: Determine how deep and wide the ransomware has infiltrated. This step is crucial for immediate containment.
- Disconnect Affected Devices: Sever connections of impacted devices from the main network to halt ransomware propagation.
- Backup Protection: Ensure your backups, both offline and online, are isolated to prevent them from becoming ransomware targets.
2. Assess the Damage
- Strain Identification: Pinpoint the specific type of ransomware used. Each variant has its characteristics and potential weak points.
- Data Encryption Extent: Understand which files, databases, or entire systems have been compromised.
- Backup Security Check: Ascertain the integrity of your backups. They’ll be your primary tool for recovery.
3. Execute Your Response Plan
- Data Recovery: Use available backups to restore encrypted data wherever possible.
- Decryptor Utilization: For certain ransomware strains, third-party decryption tools can be an avenue for data retrieval.
- Engage with Authorities: Involving law enforcement can provide resources, further investigative depth, and insights into the ransomware group’s tactics, techniques, and procedures (TTPs).
- Ransom Payment: Though it’s not universally recommended or always legal, sometimes the situation may necessitate considering paying the ransom. Consult with legal authorities and cybersecurity experts before taking this step.
4. Analyze Your Organization’s Security Posture
- Post-Attack Audit: Dive deep into how the breach occurred. Understand the vulnerabilities that were exploited.
- Learn and Adapt: Use the incident as a learning experience. Bolster defenses to prevent a recurrence.
Secure against future ransomware attacks
Your organization’s assets are its lifeline. Sign up for a free trial and see firsthand how Flashpoint cybersecurity technology can help your organization access critical information and insight into ransomware actors and their tactics, techniques, and procedures (TTPs).
Get the latest news and insights delivered to your inbox.
Interested to see top news from Flashpoint hit your inbox directly? Subscribe to our newsletter to receive curated content on a regular basis.


